3.1.4
Identify the technologies required to provide a VPN.
Teaching Note:
Sample Question:
JSR Notes:
JSR point: network pictures or videos reminder.
(For additional information, by way of an introduction, I can whip through a PowerPoint presentation on my hard drive: VPN_Technology.ppt on my hd.)
VPN Basics
Recall the various kinds of networks from the 3.1.1 notes and the diagram for VPN:
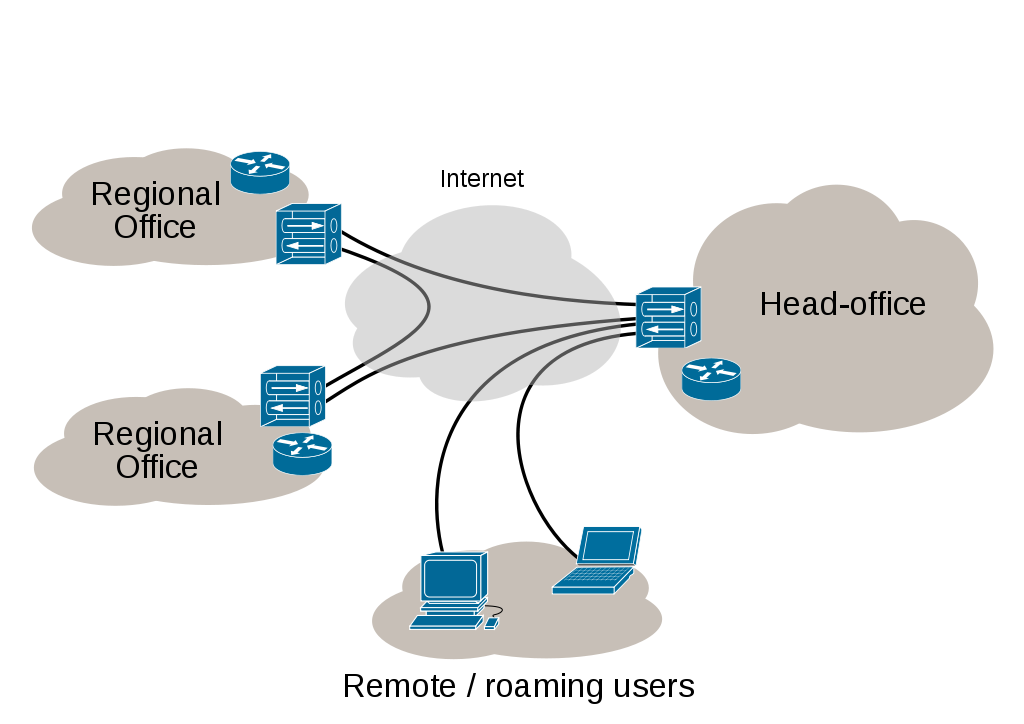
The basic idea is that you use existing network infrastructure to make a "virtual" network running over top of it, and you do so securely by both "tunneling" through it, and encrypting your data that is sent through it. "Virtual" means that it seems to be your own private network that others cannot see into, but yet it is actually not a separate, secure network. There are no dedicated leased lines, i.e. cables, that are dedicated to this network alone; rather, the network is virtual. (Think of other uses of the word virtual: virtual reality, virtual high school, or a topic we covered recently, virtual memory - these are things that seem to be something, but really are not.)
Here's a good, slick video about the basics of what a VPN is.
Large Scale & Small Scale VPNs
Companies Use of VPNs
Often companies will use VPN technology to set up large scale VPN networks for their employees, so that they can work in various geographic locations, but still be sharing a safe, private network. These are referred to as Site-to-Site VPNs, and along with enabling remote connections for traveling employees, these are primarily set up to provide encrypted pathways between different LANs the company operates in different geographic locations. This gives the company the same capabilities as private leased lines at much lower cost by using the shared public infrastructure. (Note that this is not the same thing as WANs, in which dedicated communication lines are set up and/or leased. There are obvious cost benefits to the VPN option, but more security with the WAN option.)
Individuals' Use of VPNs
On a much smaller scale, individuals or small groups can use services to quickly set up small VPNs for a variety of purposes. We can categorize them as full VPN services, and proxy services. Full VPN services are used primarily for remote connection, and include the use of "remote desktop"s. And proxy services primarily only mask who you are over the network.
Full VPN services will offer all types of VPN advantages by making your computer seem to be part of a large network that has multiple resources. It will seem as if your computer is part of that full network, with all its devices and resources - so you can log into other computers on that network, take advantage of shared data and applications, use printers and other shared hardware resources, and anything else provided by that virtual network. Examples of subscription based (full) VPN services include:
- NordVPN
- Express VPN
- PureVPN
Primarily Remote Desktop Apps - this is usually a one-computer-to-one-computer connection. Individuals will use these services for controlling one of their other devices remotely, so for example, controlling their home computer from work, or vice versa. Another common use of remote desktop applications is when a technician takes over your computer remotely to fix it. It seems like he/she is right there, managing your computer, as the mouse magically moves around while they control, and fix your computer. Examples include:
- LogMeIn.com
- TeamViewer
- AnyDesk
Primarily Proxy Services - use of a proxy server is simply routing your Internet activity through another server. A proxy server can be used for a variety of reasons, such as pretending to be connecting from a different country so you can access content blocked in your own country, taking advantage of the proxy server's more robust filtering and/or protection, or simply to disguise your identity by using the proxy server's IP address instead of your own. Examples include:
- HideMyAss.com
- Tor Browser
- Hotspot Shield
Also note that now, some browsers now support VPNs as part of their core functionality. For example, the browser Opera.
__________________________________________________
VPN Technologies
(For the technologies of VPNs, this time, I'll actually start with the summary, and then go into more details.)
(Also, note that nothing above is actually specifically required for this assessment statement - though it helps with the next one, and the context for this one is surely important. But the section that folows is actually all that this assessment statement asks for; it's simply an "identify" assessment statement.)
Summary of The Technologies Needed for VPNs (Virtual Private Networks)
You can - for your canned answer - simply identify (if that's all the assessment statement asks) the technologies needed for VPNs as:
- Hardware Technologies Needed for VPNs:
- A server to connect to the network: "Network Access Server" (this could simply be your laptop connected to the Internet)
- A VPN Tunneling Server, so for example, a "PPTP server" (this could simply be your laptop with VPN client software installed)
- VPN Software Technologies:
- tunneling
- encryption
- Examples of Protocols Used for VPN connections:
- PPTP
- or SSL
- or L2TP
(Again, remember that this assessment statement is that it's an "identify", so there's no need to go into great detail about how any of these work and/or are implemented; rather you just need to be aware of them, and roughly what they mean; never-the-less, a bit more is surely desirable, so read on.)
Details
The prime feature of a VPN is that it is secure. The security is created on two levels. At the network level, a separate, secure "tunnel" is effectively made through another existing network. And at the data level, the data itself is encrypted. An analogy of this double protection could be a thief in disguise sneaking through a secret tunnel.
We can break down the technologies needed for VPNs into three categories: Hardware, Software/Algorithmic, Protocols.
Hardware:
- Network Access Server - at both ends of the connection there needs to be a way to access the Internet (or other network the VPN is running over), so this is a term we can use to refer to all such devices, whether they be your router at home, or a gateway server at a big company.
- VPN Tunneling Server (or, specifically, a PPTP server - refer to the PPTP section below), which will be what the company/organization has to allow PPTP tunneling through the Internet to work. So the company/organization will need to have both their regular Network Access Server, and a PPTP server in addition.
- if you are using a software based VPN, your computer will be acting as the PPTP server, so it has some limitations compared to an actual hardware PPTP server of a company or organization.
- if you are using a software based VPN, your computer will be acting as the PPTP server, so it has some limitations compared to an actual hardware PPTP server of a company or organization.
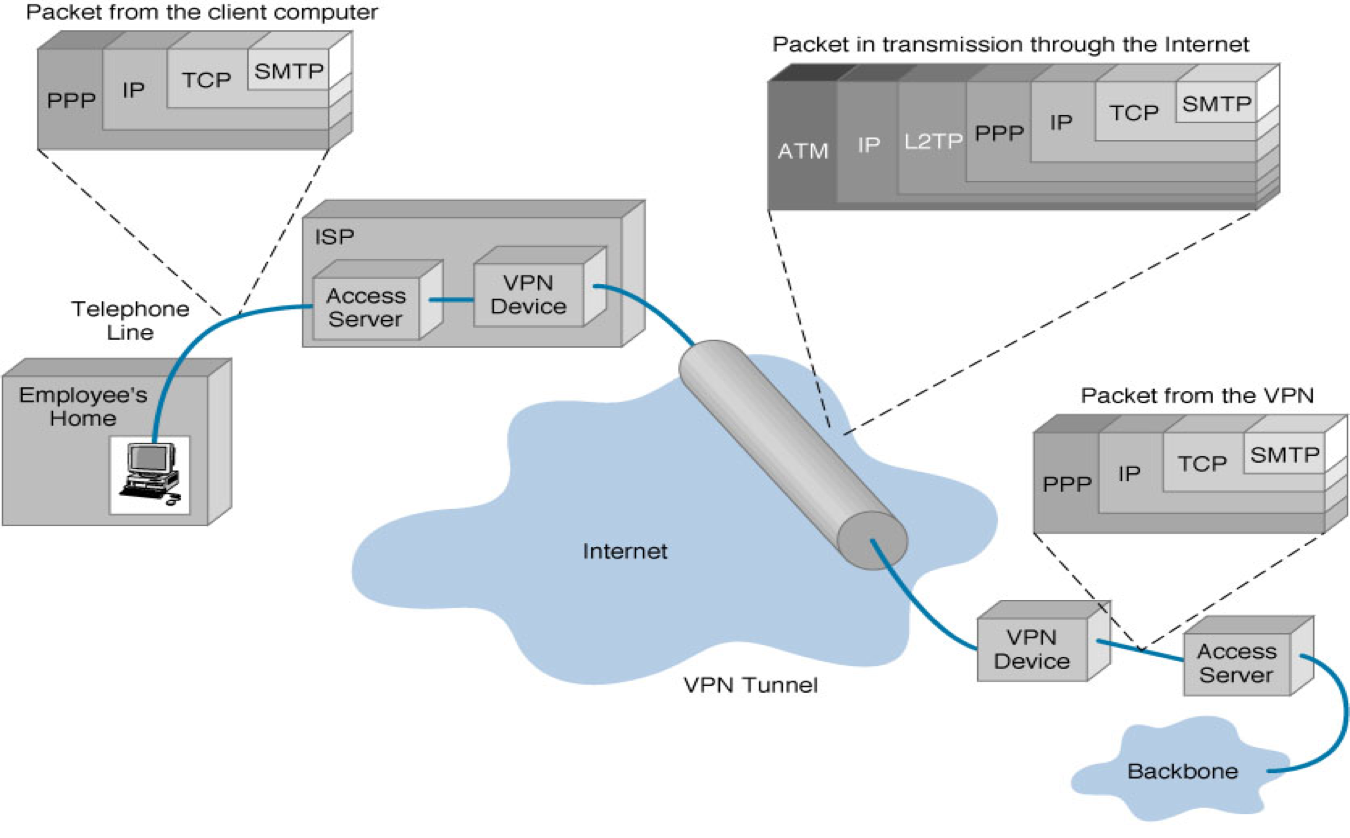
(Don't worry about the details of this diagram, just get the general drift that a lot of stuff being sent is encrypted, and that there needs to be a PPTP server (here labeled VPN Device) at both ends of the connection.)
Software/Algorithmic:
- Tunneling - This is the term used for establishing a secure connection through another network (such as the Internet) using the hardware and protocols such as those described below. An "onion layer" is created over the existing layer. (Think of onion layers; the first example of this was TOR, developed by the US Federal Government).
- Encryption - scrambling of a message a certain way, which can be unscrambled if you know how it was scrambled in the first place.
- So, a simple example would be add one ASCII value to each letter ("hello" becomes "ifmmp"), so to unencrypt it you would subtract one ASCII value from it (so "ifmmp" become "hello"). But the algorithms for encrypting are extremely complex and (hopefully) impossible to hack.
- a simple explanation
- wikipedia: sha 256 encryption technique (look for the pseudocode to see how complex a scrambling it is)
- times to "brute force crack" of an encrypted password.
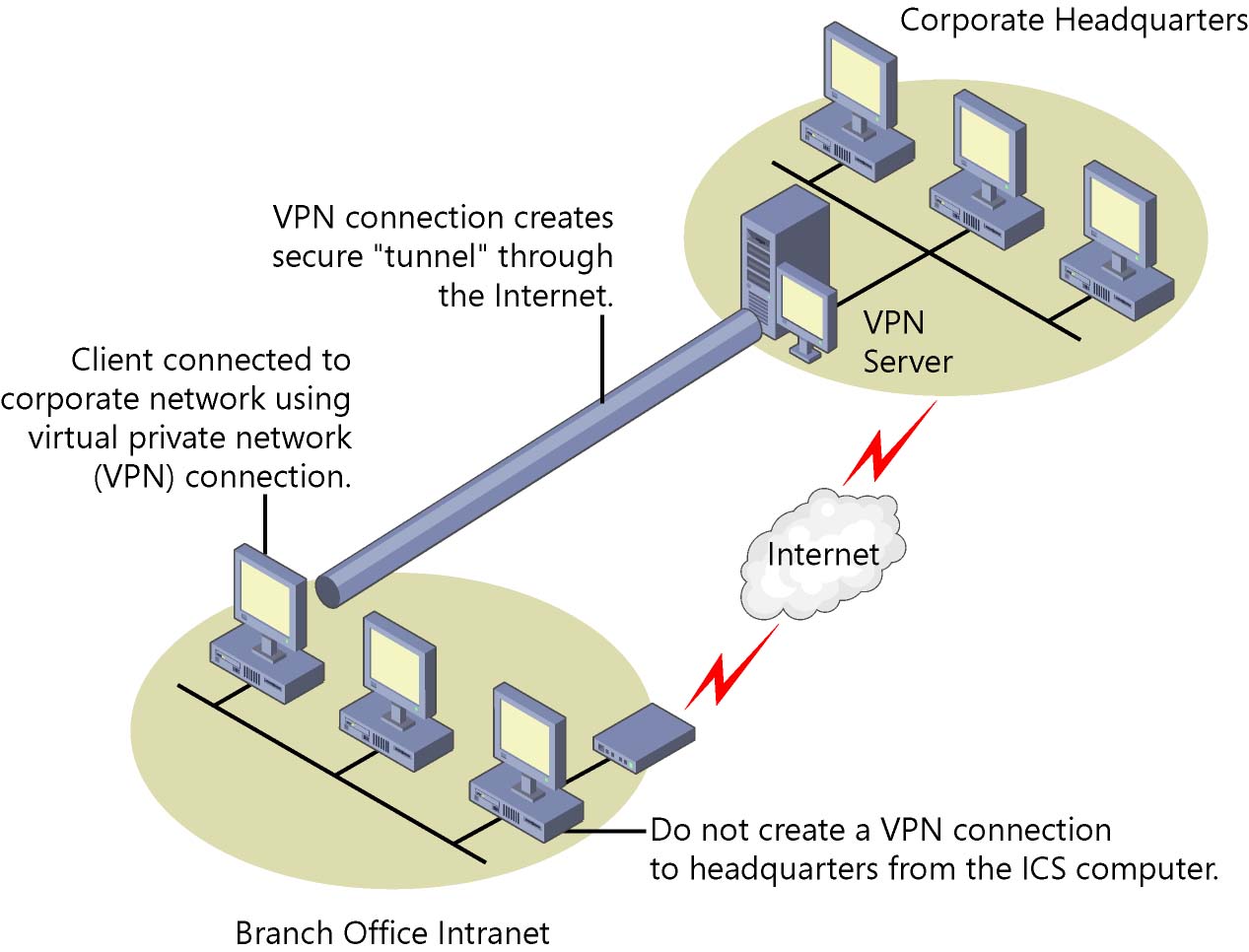
Protocols:
Firstly, a reminder of what a "protocol is": it is an (often internationally) agreed upon set of policies and procedures, usually related to some sort of communication or interchange. There are protocols for all sorts of things, not just technology, like the way that visiting dignitaries to a foreign country inteact with various other leaders. The other main networking protocol we have looked at in this Topic 3 is TCP/IP protocol of Internet communication.
So now onto the protocols followed/used for VPN connections. There are three good examples of protocols commonly used:
- PPTP - Point-to-Point Tunneling Protocol - this is one of the most common protocols used for controlling VPN sessions. It was developed by Microsoft and can be used by Windows machines.
- L2TP or Layer 2 Tunneling Protocol (L2TP) is the result of a partnership between two companies, Cisco and Microsoft. It was created to provide a more secure VPN protocol than PPTP.
L2TP has all the features of PPTP, but runs over a faster transport protocol (UDP). But it is still overall slower than PPTP because it encrypts data using a much more strong 256-bit encryption system, which uses significantly more CPU power than PPTP.
- SSL (Secure Sockets Layer virtual private network) is a form of VPN that can be used with a standard Web browser, so it is not Windows specific, and does not require a specialized servers, like PPTP or L2TP do. A good example of a site that uses this for secure transactions is Amazon.com.
Good brief SSL explanation
* Note that Tor (from it's original name "The oninon router") is not a VPN service. There is no security/encryption involved. It simply provides anonymity for those who use it, via an "onion" layer made by volunteers who are part of the community and who supply and manage the 7000 or so relays of this "onion skin" over top of the Internet.
_____________________________________________________
And, back to the assessment statement, remember that in terms of the overall structure of an answer on an exam regarding this assessment statement, it should be something like this:
- The technologies required to provide a VPN can be organized into software/algorithms, hardware, and protocols. Software/algorithms required include...., hardware includes... and protocols include... (with brief phrases demonstrating you know what each is, yet allowing you to answer within 7 minutes for a 5 mark question, for example.)
Other Links:
What is a VPN?
VPN, An intro.
Reasons to use VPNs
How a VPN works.