3.1.16
Evaluate the advantages and disadvantages of each method of network security.
Teaching Note:
Sample Question:
sdfsdfsf
JSR Notes:
1. Authentication with Accounts/Passwords/Biometrics
Strengths
- Software solution; no extra hardware needed
- Managed by individuals themselves
- It can work well for those who have good password habits.
Vulnerabilities/Weaknesses - the same thing that makes user ID/password systems strong, can make them weak.
- Poor user ID/password habits, including losing them, and not having them be secure enough.
- Weak password are prone to "brute force" attacks, where all combinations of letters/numbers/symbols are tried until the password is determined. The number of characters in a password exponentially influences how long such attacks will take, as does the breadth of keys used in the password. Check out this link to see the effect of numbers of characters, and breadth of characters used, in a password. And check out my own password management hints here.
1B. Permissions
(Again, probably not focused on with this assessment statement.)
Strengths
- Works well with User ID (Accounts) systems.
- Allows multiple users to be able to access the same files on the network or device, but at different levels; what one person can do with a file (in terms of reading and writing - i.e. editing) another may not be able to do.
Vulnerabilities/Weaknesses
- Difficult to manage various permissions, both from an OS standpoint, and a user standpoint.
- Potential corruption of permissions can cause big problems. Since they are simple small amounts of data, flipped bits can cause a Read to become a No Access, for example.
If there is an incorrect permission on a crucial file, the whole file cannot be used, and that alone can cause a whole process or program to freeze. (For example, if a Read for one of the System's "users" becomes No Access on a crucial file, that crucial file cannot be used at all.)
Here's an image that gives you a visual of how permissions can be very error prone. This is a screenshot of doing a "Permissions Check" on older versions of the Mac, and sure enough most times you ran this, there were multiple permissions which had gotten corrupted/changed.
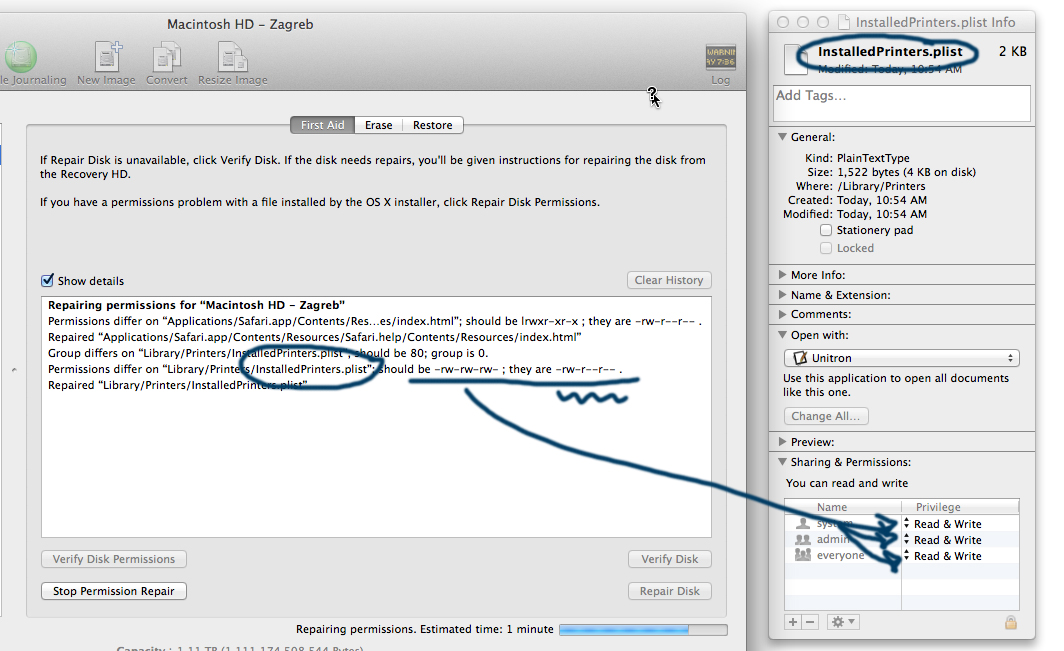
2. Trusted Media Access Control (MAC) addresses
Strengths
- Devices can be kept track of as being trusted or not. So this can prevent all sorts of security breaches.
- And also, if any mischief does happen from devices allowed access, the guilty device can be traced.
Vulnerabilities/Weaknesses
- The MAC address can be spoofed. (Though it is possible for spoofing to be detected.)
3. Encryption
Remember that encryption is particularly important for wireless networks, in which it is easy to "pick out of the air" the communication. And recall also that VPN technology relies on strong encryption, along with tunneling technology.
Strengths
- Software only technique; no extra equipment needed
- As long as the encryption method used is strong and up-to-date, it can be virtually impossible to intercept and decipher communication. (With this point, don't confuse the ability to decipher it if you have the key, versus trying to decipher it by brute force.)
Vulnerabilities/Weaknesses
- If too weak, or inconsistently used, encryption can be prone to hacking.
- Vulnerabilities can be found, eventually with all encryption techniques, and hacking can then become possible.
- Encryption slows things down, since it takes time to encrypt and decrypt (and this is a reason why sometimes people choose to forgo encryption, even though they know they should not.)
WPA-specific Encryption:
- Advantages of WPA (over WEP)
- Provides extremely strong wireless security
- Adds authentication to WEP’s basic encryption
- Disadvantages of WPA
- Generally complicated setup is required, unsuitable for typical home users
- Possibly incompatible with some older systems
4. Firewalls
Note that firewalls can be relatively basic software solutions, all the way up to sophisticated hardware solutions. The relative strengths and weaknesses of a particular solution are primarily influenced by the type of firewall they are.
Strengths
- User level firewalls are often free and with no extra equipment; in fact, often incorporated in the OS.
- Easy to implement, when intended for personal use only, as part of the OS, or a security suite such as Avast.
- Expert hardware firewall systems are as comprehensive and good protection as you can get.
Vulnerabilities/Weaknesses
- User level firewalls can be breached, if not kept perfectly up-to-date, and current to the latest kinds of malware attacks.
- And they can unacceptably slow down all Internet traffic, at least lower quality ones.
- The best hardware solutions are very expensive - the best "enterprise solutions", which provide both excellent protection, and also smooth traffic, are expensive to buy and maintain, via the service contract and its continual tweaking (hundreds of thousands of dollars per year).