3.1.15
Describe the different methods of network security.
Teaching Note:
Include encryption types, userID, trusted media access control (MAC) addresses.
S/E Wireless networks have led to concerns about the security of the user’s data.
Sample Question - FORMER CURRICULUM:
A small company has a LAN connecting its various desk-top computers and
peripheral devices.
(a) Explain, with an example, how handshaking might be used during data
transmission over this LAN. [2 marks]
The company is going to provide Internet access to its LAN.
(b) State the name of an additional hardware device that would be required to permit
Internet access. [1 mark]
(c) Explain how a firewall would help to provide security for the LAN. [3 marks]
(d) Suggest, with reasons, two further measures that the company should take to
safeguard its data from unlawful access via the Internet. [4 marks]
JSR Notes
This is a huge area. So for sure, we'll focus on what the Teaching Note refers to: encryption types, user-ID, trusted media access control (MAC) addresses, but we'll add other important security measures too, noting that the Teaching Note says "include..." Those, though, I'll dark-grey out. Your strategy could be to learn these, if you already have an idea about them, and so you can have them ready too, for a big question on network security.
Wired and Wireless Security...
Note that a fair amount of this applies to the security of wired networks too, in the same way that there was a lot of overlap with wired networks when we did hardware associated with wireless networks. ***And***, an important note in the Teaching Note, is that it says "network security", not just "wireless network security", so even though this part of the curriculum focuses on wireless, we're back to wired too.
Though, keep in mind wireless security issues are still more concerning than wired security
Wireless network devices use electromagnetic waves (usually radio waves or microwaves) to communicate with each other, and these, freely flowing through the air, can be intercepted. So any information that is unencrypted can be read, including passwords, which, when obtained can allow the hacker access to your on-line services, gaining your personal and confidential information, and/or stealing your identity.
JSR teaching note: start with a nice board diagram of "Me & My Device/data, with an arrow away: data encrypted, and three arrows in, blocked: bad folks, bad devices, bad websites (authentication, MAC addresses, firewalls)...
1. Authentication using User ID & Passwords / Biometrics
One means of achieving network security is by controlling who has access to devices and files. "Authentication" is the process of a user proving who they are. Authentication can be used to grant access to:
- certain devices
- specific levels of access of devices, i.e. access to particular files, directories or services
- particular websites/portals
Authentication, can be achieved with either a combination of user ID & password, or via some sort of biometric, either of which can confirm the user's identity.
Passwords - If the system uses passwords for authentication, the user needs to do a good job of choosing secure passwords, and keeping other good habits like not sharing them or writing them down anywhere.
Biometrics - Forms of biometric authentication you may be familiar with, include facial recognition, and the Touch ID of your laptops, but there are many others.
User Accounts allow management of access to files
Once access has been granted via authentication at login, access to files and services is controlled by an overall accounts system, similar to the one that you probably use on your home computer, or have used in computer labs at other schools. You log in as a specific user and are given a certain level of access to files.
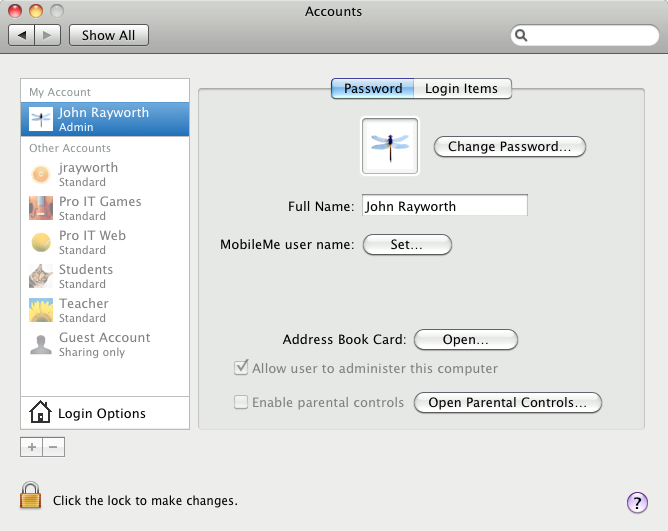
The Mac System Preference Users & Groups showing the various accounts
Above are the users on a lab computer I once used for teaching various courses. The only user account that is an "Administrator", with the highest permissions, is my own account. All the other student accounts had very limited permissions and access, since students weren't supposed to be changing system-wide settings, or working with of other students' files.
And below is a screen shot showing how, when logged in as one user ("johnr" in this case), other users' files are inaccessible (like the files of the user "justtesting").
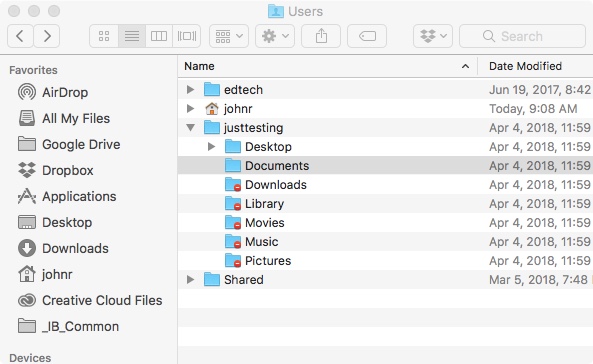
Folders of a user account not presently logged into
1B. Permissions – Firstly, note that this is not likely meant to be very much of a focus with this assessment statement. Never-the-less, knowing how permissions work will help your overall understanding of accounts systems, since they play a key role.
The security of the above system of login and passwords is practically implemented via various files having certain permissions, which, for a particular user allow:
- full access: both "Read" and "Write"
- partial access, either:
- "Read only" (this is not just "reading", this is opening)
- "Write only" (this is not just "writing", this is making changes to it)
- no access
And even when logged in as a certain user, specific permissions of files can be altered to add extra security, for example in a case where you regularly let someone else be logged into your account, but want to prevent them from accessing certain folders.
Below is a screen-shot of the permissions of a file (bottom part, greyed out):
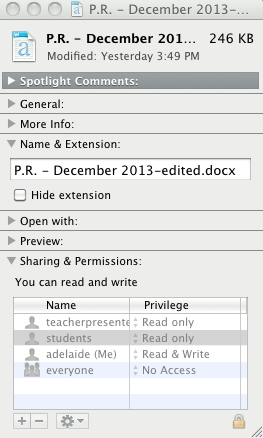
The above file cannot be opened by "everyone", but the "teacherpresenter" and "students" users can "Read only" it, meaning that they can open it but not make changes. And the user "adelaide (Me)" can both read and write to it, meaning that user account can make and save changes to the file.
This is the same basic idea as giving different permissions to documents and folders on Google Docs.
2. Trusted Media Access Control (MAC) addresses
Another way of assuring network security is to be very careful about which devices (not necessarily which people) access the network. This is done by limiting the devices that can connect to the network to devices know to be safe. This is done via monitoring their MAC address.
The MAC address is the unique address of a specific individual piece of hardware. It is based on a serial number or some other piece of information that is encoded permanently on one of the device's ROM chips. A network can therefore have a list of trusted devices, and allow only those to access its services.
Technically, the Media Access Control (MAC) Layer is one of the two sub layers that make up the OSI model’s Data Link Layer, in which data packets are moved to and from one Network Interface Card (NIC) to another through a shared channel.
Note that the MAC address differs from the IP address. Whereas the MAC address is a permanent hardware number associated with a specific device, like a computer or a phone, an IP address is something that is assigned to a device for the purposes of transferring data, through the TCP/IP protocol. IP addresses of individual devices can vary, depending on the system being used, and one device, which has various functions, may have more than one IP address.
Also note that there is a problem with the MAC addresses, and that they can be temporarily, but easily, spoofed. Through some very simple Terminal etc. commands, a user can change the way the MAC address is seen by other devices and servers on the network, though, fortunately spoof detection is also possible.
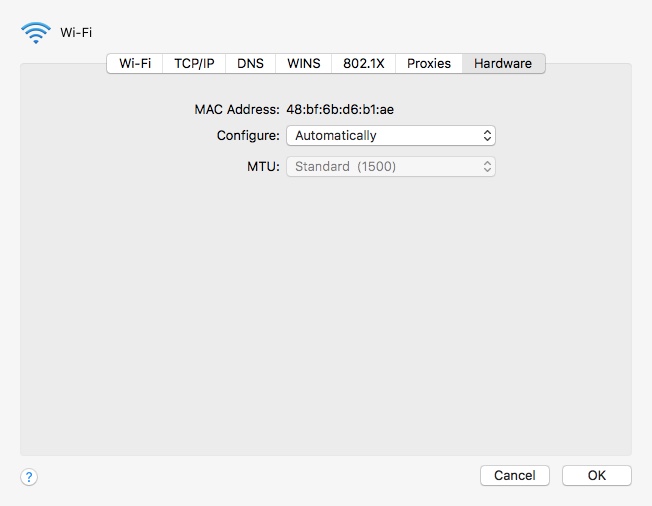
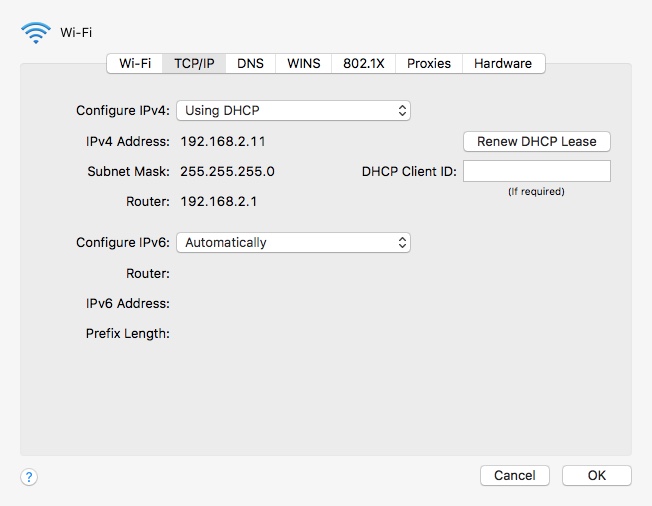
The permanent MAC Address of the device, below.
vs.
An "dynamic" IP address assigned by the network DHCP server, above.
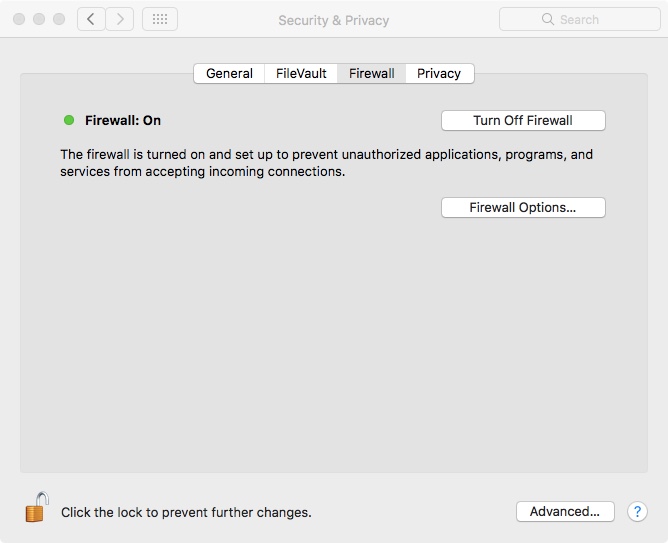
3. Firewalls
To assure network security, not only can you monitor and control the people, and the devices connecting to your network, but you can also montor and limit the networks and websites your network is allowed to interact with. This is done via a firewall.
A firewall is basically a list of "good" IP addresses to which it will allow access to the computer or network it is protecting. This list is often referred to as a "whitelist". Often times the main firewall of a full LAN will reside on the gateway computer, or even be a separate piece of hardware working with the gateway in the Demilitarized Zone (DMZ). (The DMZ is the unprotected entryway of a network; the subnetwork which can interface with outside untrusted networks, i.e. the Internet).
And for individual personal computers, the firewall is usually only a software firewall, either part of the operating system, or one that comes with a security suite such as Avast or MacAfee. By only allowing white-listed addresses to access the device/network, the firewall filters out and prevent access by known and unknown malicious or infectious sites, and it also prevents hackers from directly accessing the device or network.
4. Encryption – In a nutshell, this is simply the scrambling of the data before it is sent. The only way the receiver of the data can un-scramble the data is with a certain ‘key’ that only he/she is entitled to. You could come up with all sorts of weird and wacky ways to scramble and unscramble words; it’s just a matter of coming up with a specific algorithm to do so, and also figuring out the algorithm to take it back to the way that it was. From the time of the Romans to present-day encryption methods used for BitCoin, people have always had a reason to hide information, which can later, or by someone else, be "un-hidden".
One simple example of an encryption "scrambling" technique would be to add 1 integer value to each character in a String. So "abc" would become "bcd". To reverse the encryption you would subtract 1 integer value from each character in the encrypted word. So "bcd" becomes "abc" again. You'll note that when encryption is done with a certain mathematical algorithm, even a simple one like this, that algorithm is called a "hash" (*see details in the Not Necessary section at the bottom of this page).
One common method to achieve encryption is symmetrical encryption, where both parties share a key. To do this securely, one way is to convey they key over the phone. To get around this need, there is public key encryption (also known as asymmetric encryption). With this, a public and private "key" is shared only by the sender and receiver, and is necessary to be used as part of the decryption algorithm to decrypt the message. How the private key is kept private, yet able to be shared is complicated, but possible (see videos below if you want to try to understand it.)
For example, the key could be 7 5 9 2 3 4. That, used in conjunction with a simple encryption algorithm, could encrypt a string like "abcdef" by doing the following with the key: take each of the integer values of the key, and shift the ASCII values of the characters in the message, one after the other, by those values. So 'a' gets shifted by 7 to 'h', 'b' gets shifted by 5 to 'g', and so on.
This would result in an encrypted message: hglfbj. So since the receiver knows the key, and the decryption algorithm to follow using it, decryption would reverse the process, yielding the original "abcdef".
Above, two basic explanations of private key encryption.
And a more sophisticated way of looking at it. Plus, the actual sophisticated mathematics of it.
Wireless Encryption Protocols
- WEP (Wired Equivalent Privacy)
- An older encryption protocol still a necessary option for older devices, but less secure than WPA & WPA2.
- WPA (Wi-Fi Protected Access)
- Encrypts the information and assures that the encryption key cannot be modified.
- It also authenticates the users to assure that only authorized people can access the network.
- WPA2
- Newer and more secure than WPA
- But may be incompatible with older network hardware.
And finally, with encryption, do note that strong encryption can have a tendency to slow down things, but with modern computers, this shouldn't dissuade the use of the strongest encryption possible.
Authentication vs. Encryption
If you are getting into the finer details of some of this, be careful not to confuse authentication hashing techniques and encryption. With authentication, a person will often type in a password, but what actually gets stored on the back-end database is actually not that password, rather it is a hash of it. A hash is a *one way* function, which changes a string of characters into a certain "hash result" string, which shows no relation to the password, and which cannot be "backward" calculated to the password. This is useful in authentication, where a hash will be applied to a password, and it should result in the stored hash result to prove the user typed in the correct password. Sha256 is an example of such a hash function.
Meantime, encryption/decryption is a two-way function, in which a message is scramble, and then "de-scrambled", or encrypted/decrypted. The message is readable, therefore, both before it is encrypted and sent, and also after it has been decrypted at the other end. A private key is often used at both sending and receiving ends of the communication to achieve the complementary encryption/decryption.
The key: And with the key, note that it really is, for all intents and purposes, impossible to crack within any reasonable amount of time. The RSA encryption private key is 128 bytes, or 1024 bits. Two to the power of 1024 yields a decimal number 309 digits long! Try brute force guessing that!! BTW, if you take a look at a stored private key, for example in some configuration file, it will come out as way more digits than that, since it, itself, is stored and displayed in an encrypted way for security purposes.
We have already encounters (non-wireless) encryption that is used in the following protocols: PPTP, L2TP, and SSL. And in terms of authentication, a few specific cryptographic hashing algorithms you might also encounter include Blowfish, MD2, Sha 1 and Sha 256.
5. Other/Miscellaneous (likely beyond what we need to cover, but included for a sense of completion)
- Not allowing the downloading various kinds of executable files (at least, certainly not from unknown sources). Executable files have extensions including .exe (Windows applications), .app (Mac applications), .jar (compressed Java files), and .bat (Windows batch files that are scripts for running System commands). Executable files could run viruses or other malware.
- Two factor (or two step) authentication - here, not only do you type in a password, for example, but there is an additional step of authentication required (i.e. proving you are you). This can be done via the software interface, for example answering a security question, such as "What was the name of your first pet?" But two factor authentication is best done via a second device. So you log into your bank account on your computer, for example, but to do so you need both your password, and a special code sent to your phone, or other device specifically for the purpose of receiving a "one time password" OTP.

Example of a separate device for a "One time password" as an additional step for authentication
- Isolation - a technique in which a wireless router places all wireless connections on a "subnet" independent of the primary network. That way your private network data is isolated from pass-through internet traffic.
- Hidden SSID - every wireless access point on a wireless network (like the one you can see attached to the ceiling of the classroom) has a Service Set IDentifier (SSID), which by default is broadcast so that the access point can be found by potential clients. (This is the list of Wireless devices you see when you search for a WiFi connection.) It's a good idea to disable this feature so that standard client connection software won't be able to "see" your access point. This doesn't keep expert hackers away, but at least it keeps the access point name out of sight of casual wireless users. (Think: "out of sight, out of mind".)
Jaime: TOR example - 7000 or so volunteer servers around the world have made an "onion" layer over the Internet for those who want to remain anonymous.
"Hash salting" adds bits randomly through the encryption
------------------ NOT NECESSARY - EXTRA -------------------
*More on Hashing
Recall from the dark grey section above, whereas with encryption, the scrambling can be unscrambled by anyone with the key, good hashing algorithms result in something which cannot be "un-hashed". The purpose of a hash is to be able to tell if a message has been tampered with (in this case as part of network activity). When the hash is applied before and after transmission, the result should be the same, but it will be very much different if a modification has been made, therefore acting as a flag to improper (in this case network) activity.
A lot of time and energy is spent by agencies like the US government's NSA (National Security Agency) to come up with increasingly secure hashing techniques which are as close to being un-crackable as possible. Examples are sha1, sha128, and sha256. To see how complicated these algorithms are, you can find the sha256 algorithm at this wikipedia page; it's in pseudocode half-way down.
Here is an image of the sha1 hash results to passwords on my website. I only keep the hash, so cannot "un-hash" them and know your passwords. When you type in your password, logging onto my website, the hash is applied, and it must equal the hash result I have stored for you to get in. (But, again, what is the starting point if this hash result is virtually impossible for me to ascertain.)