6.1.9
Outline how an operating system hides the complexity of the hardware from users and applications.
Teaching Note:
Students should be aware of a range of examples where operating systems virtualize real devices, such as drive letters, virtual memory, input devices, the Java virtual machine.
INT Issue of localization causing compatibility problems between systems in different countries.
Sample Question:
sdfsdfsf
JSR Notes:
Hardware Complexity Hidden: Introduction
Ease of use
A good way to frame this assessment statement point is to remember that one of the main aims of the operating system is indeed to cut down on the complexity seen by the user, and thereby making the process of using the computer easier and more straight-forward. Looked at negatively one could argue that modern operating systems "dumbs down" the skills and knowledge needed to operate a computers. And true as this may be, we do want our devices to be easy and efficient to use.
It is not just the complexity of hardware of a device that is hidden; the complexity of underlying software itself can be hidden by well developed GUI software interface. Do note, though that the focus of this assessment statement is on hiding the complexity of hardware only.
So for example, the user need not know whether the memory that a particular application is using is real (RAM) memory or virtual memory - it's like the OS is saying "No, no, don't worry about those details, I'll handle that; you just go about what you were doing..."
Connection to Abstraction
If any of this sounds familiar, it should, because this really another example of abstraction, where the details of a complex entity/situation are purposefully ignored/hidden. Through all applications of abstraction, we get to look at and deal with only one essential level of a problem at a time. In this case we can see the interface of the OS as being a veneer over the inner workings of the computer, both in terms of hardware and software.
"Virtual"
A key term here is "virtual". Virtual simply means not real; not the actual (more complicated) situation.
__________________________________
Teaching Note example 1:
Drive Letters
Drives "C", "E", "F" etc.
What is meant by "drive letters" in the teaching note is simply the C: or E: that we see representing our hard drives or other devices on a Windows computer. (The primary hard drive of a Windows machine is usually called the "C" drive: originally "A" and "B" were reserved for floppy disk drives - back in the day, you started up your computer by loading the OS from a stack of floppies!)
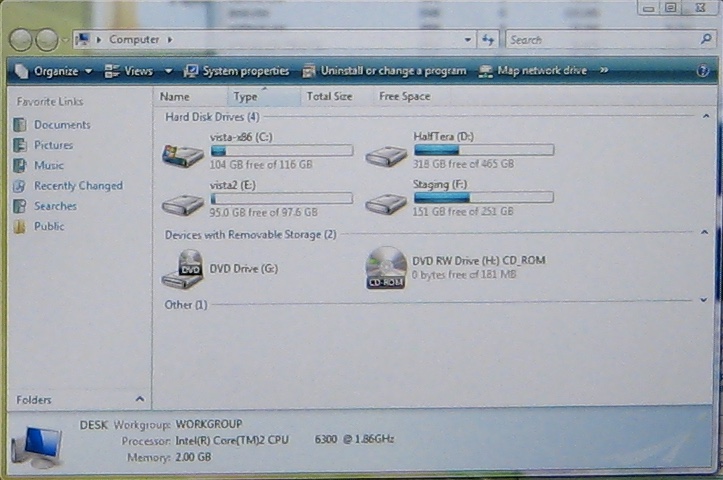
Windows Explorer With Drives
CC jeffwilcox
The hard drive is a very complicated piece of equipment, and the organization of its data is quite sophisticated, but all we need to know/see is it's name "C", and the name of the folders and files as represented to us logically in the Windows Explorer (or indeed in the Mac Finder). The logical organization as we see it need not reflect the actual organization "behind the scenes".
In fact, even though in Windows Explorer you may see "C" and "D" and "E" drives, they may all be on the same physical hard drive, or separate ones, but that doesn't matter to you. All that matters to you is that you have your System files on C, your music on D and the server provided by your company is E.
It's guaranteed that the physical organization of the data on the hard drive of computer is not actually as logically organized as it seems to be - in a simplified, ordered way in the Finder.
Underlying Complexity of Hard Drive Organization
Such things as the File Allocation Table, all the various pointers and addresses, the fragmented nature of files, and so on, are not what we see when we open a Finder window; that complexity is all hidden from us. In fact, there are many System files themselves which are hidden from us, and we must know some Terminal tricks to show them. Even the System Library of some versions of the Mac OS is by default hidden from users (though you can simply hold alt and click on the Finder Go menu to access it).
But Easy User Interface
All we are shown is the folders and files we are likely to use, such as applications and data files. And actually, in terms of complexity-hiding and "dumbing-down", the Mac dock is about as simple, and stripped down a representation of (in this case) applications on a computer as you can get.
Teaching Note example 2:
Virtual Memory
Hard Drive Virtual Memory as "Extra RAM"
We have dealt with virtual memory in another earlier assessment statement. Recall that virtual memory is "virtual" in that it is not real RAM, but as far as the user can see it is RAM. So here we are talking about the memory being used to store running applications and open documents, rather than storage. But it's actually the storage device (hard drive usually) that is being used as the virtual memory.
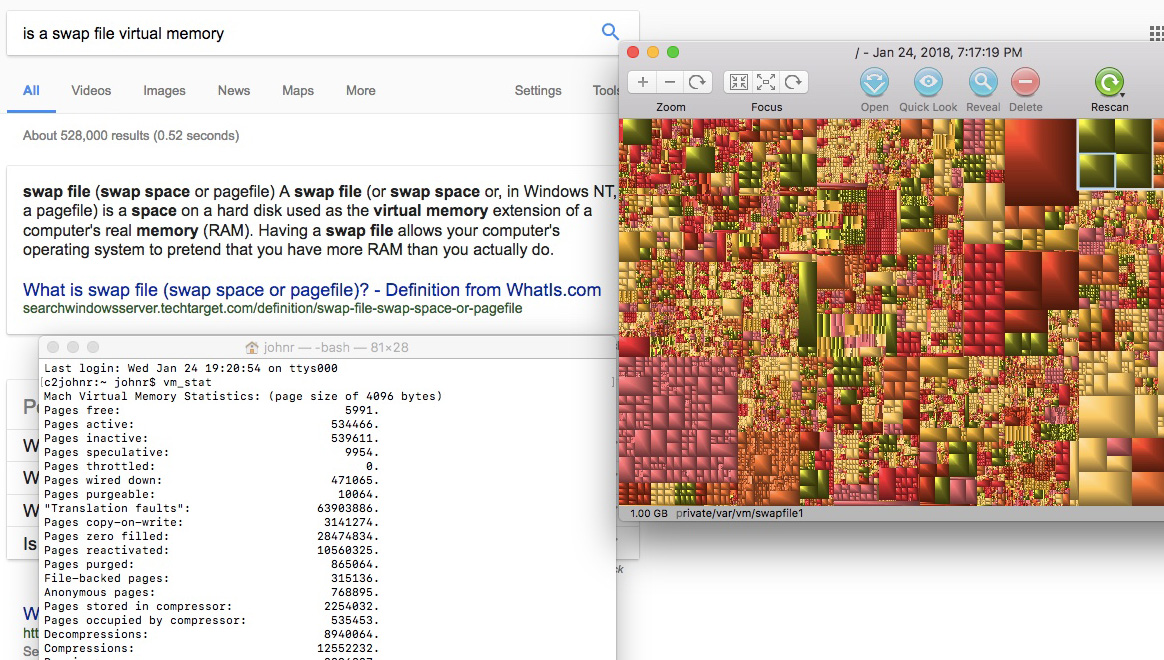
Pictured above: some VM fun on a Mac. The right hand side shows a pictorial representation of files in the hard drive (as seen from the file management application Grand Perspective); one of the four green blocks in the upper right-hand corner of it is highlighted, and you can see at the bottom of that window that it's a 1.00 GB swap file, which, as the Google search to the left points out, is basically VM. And then there's a Terminal command listing off all of the VM currently in use. (To see such a list of VM pages, in Terminal type vm_stat.)
VM to the Rescue
When the real RAM starts to get full, certain parts of applications and open data documents can get shifted into a part of the hard drive which is relatively fast. But, naturally, hard drives are slower than real RAM - the physical spinning of a disk and rotation of a read-write arm can never equal the speed of the electrical circuits in RAM.
Back in the years just before the switch from 32 bit architecture to 64 bit architecture (mid-2000s), there was by definition a 4 GB limit to RAM, since ~4GB was the maximum memory addressable (2 ^ 32 ~= 4 billion). So back then, virtual memory was a big deal, and many large applications relied on efficient use of virtual memory. Curiously though, now, with the advent of SSD drives, virtual memory can be a lot more efficient.
The fact that VM is used or not is Hidden
But back to the main point here, in terms of the assessment statement: the OS hides the fact that it is the hard drive being used as (RAM) memory along with the real RAM.
The "swap file"
The swap file, or VM space, on a hard drive is called a "swap" file because data is continually swapped back and forth between it and the real RAM memory, depending on what's most needed at the time.
Note that swapping data out of RAM to the swap file is not the same as releasing the data from memory; with swapping, the data is still logically seen as being in RAM, and physically still in working memory.
Naturally often memory is indeed freed up, most often you quit an application or you close a data file and have it saved back to secondary storage. Memory is also freed within a running Java program when variables and objects are garbage collected - you'll recall that this happens when the variables or objects go out of scope, at the end of the block of code in which they were defined. But, again, this is not moving data to the swap file; it is simply declaring that part of memory as now being free; effectivley deleting the variables or objects from working memory.
Teaching Note example 3:
Input Devices
When you plug in any peripheral, the OS looks after it. We don't have to install and deal with drivers to work with input devices such as a mouse or joy stick; the OS has the ability to handle such input peripherals. So the peripheral is just "good to go"; when plugged in, it appears on our desktop as an icon which we can double-click to open and go ahead and straight-forwardly use.
Teaching Note example 4:
Java Virtual Machine
The JVM
The "Java Virtual Machine" is a unique and complex way that the programming language Java uses to get around having to have a different version of an application compiled for each operating system. Rather, the higher level Java program is only "half-compiled" to a generic form called byte code. Then, via specific (software) virtual machines installed on specific computers, that byte code is further compiled to its final machine code state of 1s and 0s which can be read by the specific architecture of a specific computer - Windows, Mac, Linux, or whatever.
JVM Use Hidden
So getting to the point of this assessment statement, the fact that all of this is happening behind the scenes does not have to bother the user - it is for all intents and purposes hidden from them (once they first install Java on their machine).
Brief summary of the Java Virtual Machine Process:
1. When compiling a Java program, it only compiles to a general/generic form, called byte code.
2. Then, the individual machine (either Mac, or Windows, or Linux, etc.) uses it's Java Virtual Machine (which is actually software, not another computer) to translate the code into commands that particular machine can understand and execute.
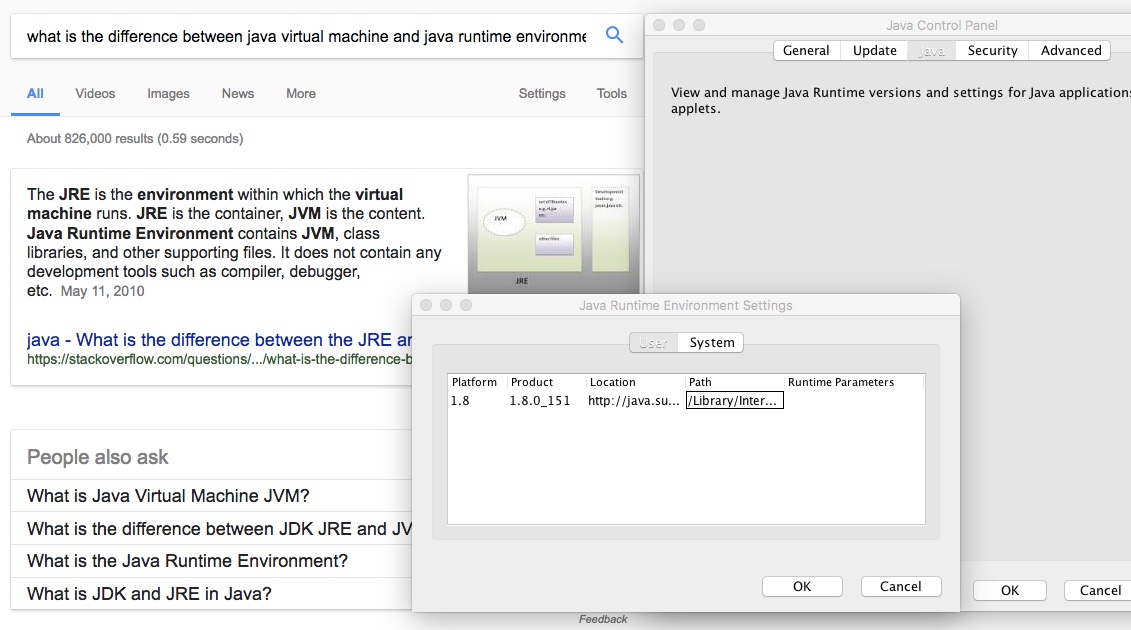
Screenshot of the Mac OS Java Preference Window (& JRE vs. JVM)
__________________________________
Other Hardware Examples:
RAID
RAID - "Redundant Array of Independent Disks". A RAID is a combination of several hard drives to accomplish one of two things, or both: backup where the same data is on two different drives, and stripping, in which data is divided between two drives, so that both reading and writing take half the time.
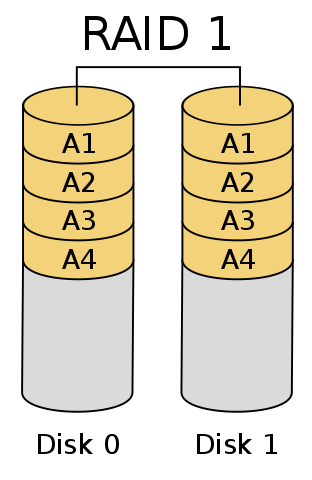
RAID 1 (Mirroring only) with two disks (disk 0 and disk 1) over one
logical volume A with all blocks replicated/mirrored from drive 0 to drive 1
CC BY-SA 3.0
RAID Use Hidden
The RAID hides the fact that you have 2, for example, hard drives (mirrored and stripped), because via your operating system, on your desktop, you just see one.

(Though, is it the RAID controller hiding the complexity or is it the OS?? Both probably.)